Solving the Lost YubiKey problem with WebAuthn PRF & Shamir Secret Sharing.
This project explores a novel approach to client-side encryption using the WebAuthn PRF (Pseudo-Random Function) extension. While PRF is typically used for symmetric key derivation, this implementation pairs it with Shamir Secret Sharing to create a robust recovery mechanism for non-exportable credentials.
Standard account recovery relies on centralized servers or passwords. While FIDO Alliance recommends registering multiple authenticators as backup, this approach proves impractical and costly for average users. Consequently, many services implement fallback authentication methods (passwords, SMS codes), creating a critical vulnerability: downgrade attacks. Attackers exploit these weaker recovery mechanisms through social engineering, with research showing 55 % of users falling for real-time phishing and 35 % vulnerable to FIDO downgrades[bicakci2022]—effectively reducing account security to its weakest link.
Shamir’s Secret Sharing (SSS) offers a decentralized alternative. Unlike standard backups that simply copy data, SSS splits a passkey’s private key into multiple unique parts called shares. This method allows for secure recovery without a single point of failure or reliance on weaker authentication methods.
Practical Implementation Architecture
Since the WebAuthn SSS extension does not currently exist in the standard, we propose a browser extension-based approach that achieves the same security goals. This system functions as a modern, passwordless identity manager with account recovery capabilities in case of hardware key loss.
System Components
Master Key (MK): A random key generated within the extension. This is the root secret that encrypts all user data (website passwords, notes, etc.).
YubiKey (Authenticator): Used to unlock the MK during normal operation via WebAuthn PRF extension.
SSS (Shamir Secret Sharing): Enables MK recovery during catastrophic failure (YubiKey loss).
Browser Extension: The orchestration layer. Performs encryption, communicates with the authenticator, and isolates the process from web pages.
Phase A: Registration (Identity Creation)
The registration phase securely creates the Master Key, encrypts it, and establishes backup mechanisms:
-
Generation: The extension generates a cryptographically strong random Master Key (MK) in memory.
-
WebAuthn PRF: The extension prompts the user to insert their YubiKey and calls
navigator.credentials.createwith theprfextension enabled.- A random salt is transmitted to the authenticator.
- The YubiKey returns a PRF output (deterministic key bound to the hardware).
-
Encryption: The extension uses the PRF output as a key-encryption key (KEK) and encrypts the Master Key, producing
Encrypted_MK. -
Backup (SSS): The extension takes the Master Key (unencrypted) and mathematically splits it into shares using SSS with threshold (e.g., 2-of-3):
- Shares are distributed across independent storage locations to prevent single points of failure
- Examples include: remote servers, physical media (QR codes, printed
backups), hardware authenticator storage (
largeBlob), or trusted contacts - The distribution strategy balances availability (easy recovery) with security (preventing unauthorized reconstruction)
-
Cleanup: The extension securely erases both MK and PRF output from RAM.
Phase B: Normal Login
Normal authentication quickly unlocks the vault using the hardware authenticator:
-
Initiation: User arrives at their device with the extension locked.
-
Data Retrieval: Extension downloads
Encrypted_MKand salt from the server. -
Key Derivation: Extension calls
navigator.credentials.getwith the stored salt.- User touches their YubiKey.
- YubiKey internally computes and returns the same PRF output as during registration.
-
Decryption: Extension uses the PRF output to decrypt
Encrypted_MK. -
Result: Extension has the Master Key in memory. User is authenticated and the extension can autofill passwords or generate passkeys.
Phase C: Recovery
Recovery enables account access when the user loses their YubiKey:
Critical constraint: Without the YubiKey, obtaining the PRF output is
impossible, rendering Encrypted_MK stored on the server cryptographically
useless.
-
Initiation: User on a new device (or with a new authenticator) clicks “Recover Account” in the extension.
-
Share Collection: Extension collects at least shares from their distributed storage locations:
- Remote shares may require authentication (e.g., email verification, OAuth)
- Physical shares require user input (scanning QR codes, entering text)
- The specific retrieval mechanism depends on the storage medium chosen during registration
-
Reconstruction: Extension mathematically combines the shares. If valid, the polynomial evaluation yields the original Master Key.
-
Key Rotation (Re-encryption):
- User is now authenticated.
- Extension prompts: “Insert NEW YubiKey”.
- Repeats Phase A process (obtaining new PRF output from new authenticator and re-encrypting the Master Key).
- Old
Encrypted_MKon server is replaced with the new version.
Security Properties
Zero-Knowledge Server: The server observes only an encrypted blob, salt, and optionally one SSS share. None of these components provide useful information without the remaining elements.
Phishing Protection: Normal authentication requires physical possession of the hardware authenticator.
Loss Protection: Hardware loss does not result in loss of digital identity (thanks to SSS).
Isolation: Browser extensions execute in an isolated context separate from web page main-world scripts[mdn_content_scripts][mdn_executionworld]. This architectural boundary prevents malicious JavaScript on compromised websites from accessing the extension’s memory space or the Master Key, even if the visited page contains XSS vulnerabilities.
Mathematical Foundation
The core of this scheme relies on polynomial interpolation. The fundamental idea is that it takes points to uniquely define a polynomial of degree .
To protect a secret , we construct a random polynomial of degree where . The polynomial is defined as:
In this equation:
- represents the secret key material
- is a cryptographically large prime satisfying
- Coefficients are chosen randomly from a uniform distribution
- All arithmetic operations are performed in the finite field
The share generation evaluates at distinct non-zero points to produce shares for .
Secret reconstruction requires collecting at least shares. Given these points, we apply Lagrange interpolation[burden2011, p. 108] to calculate and retrieve the private key[shamir1979].
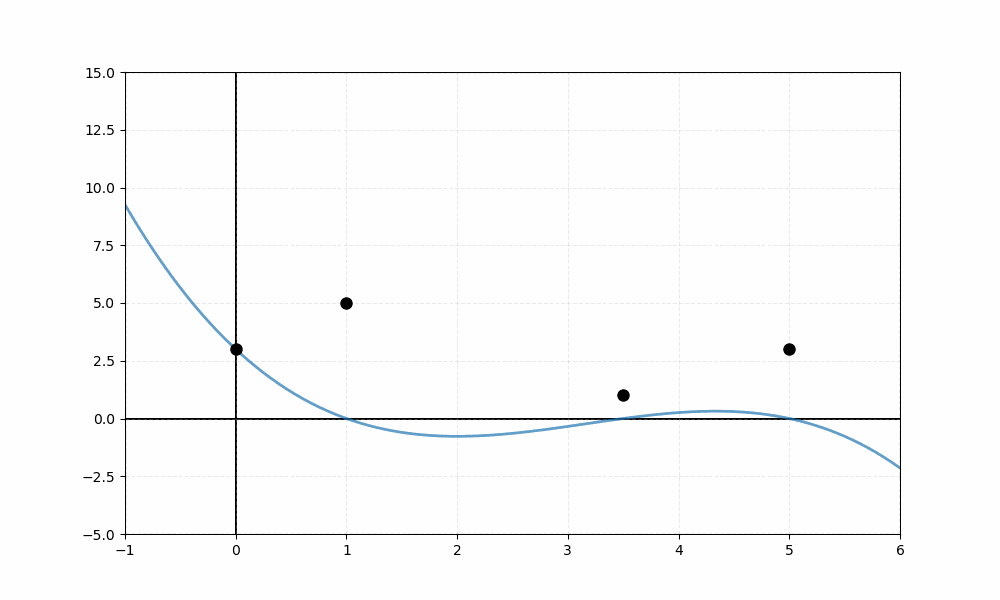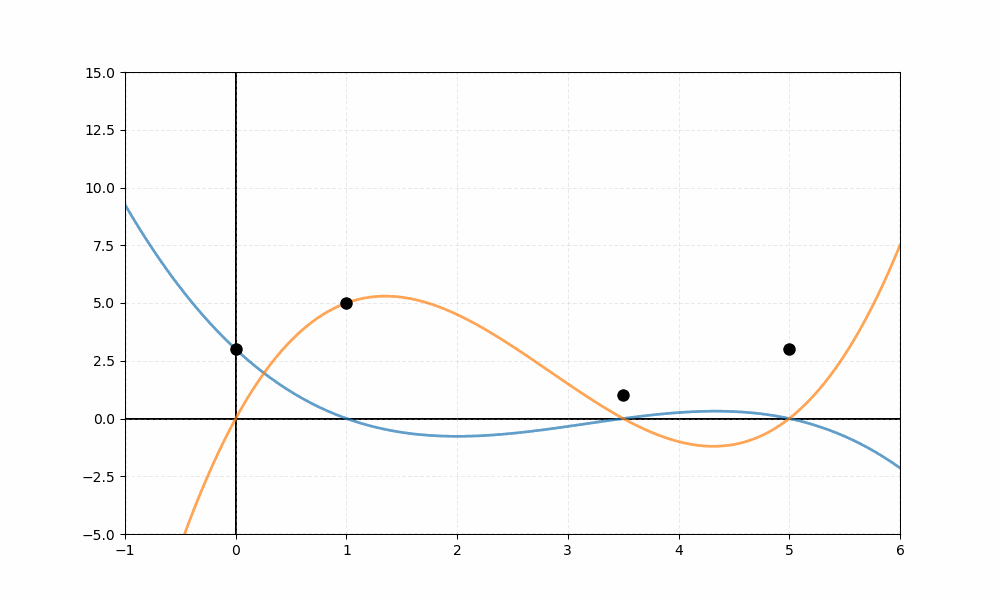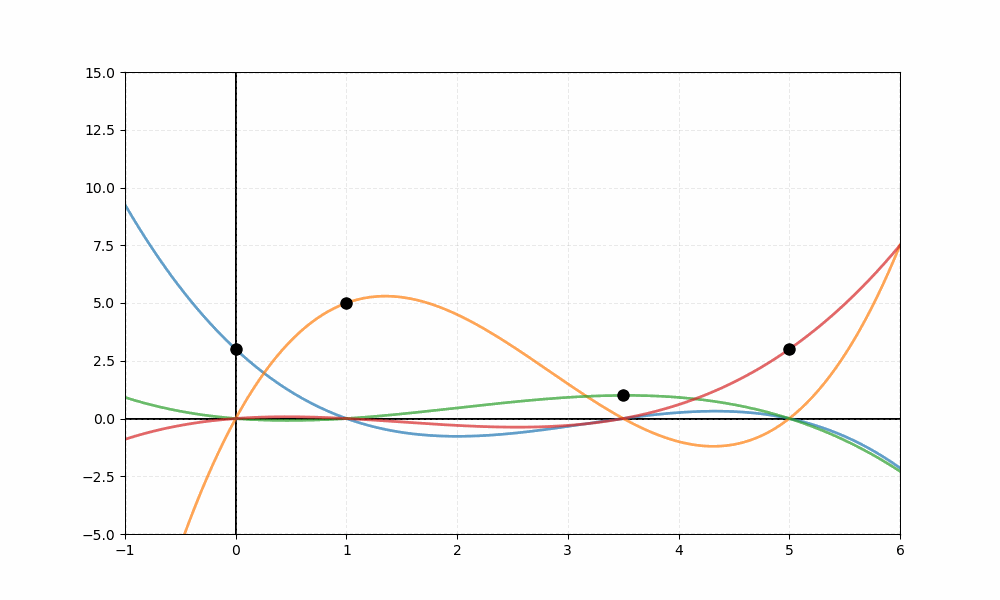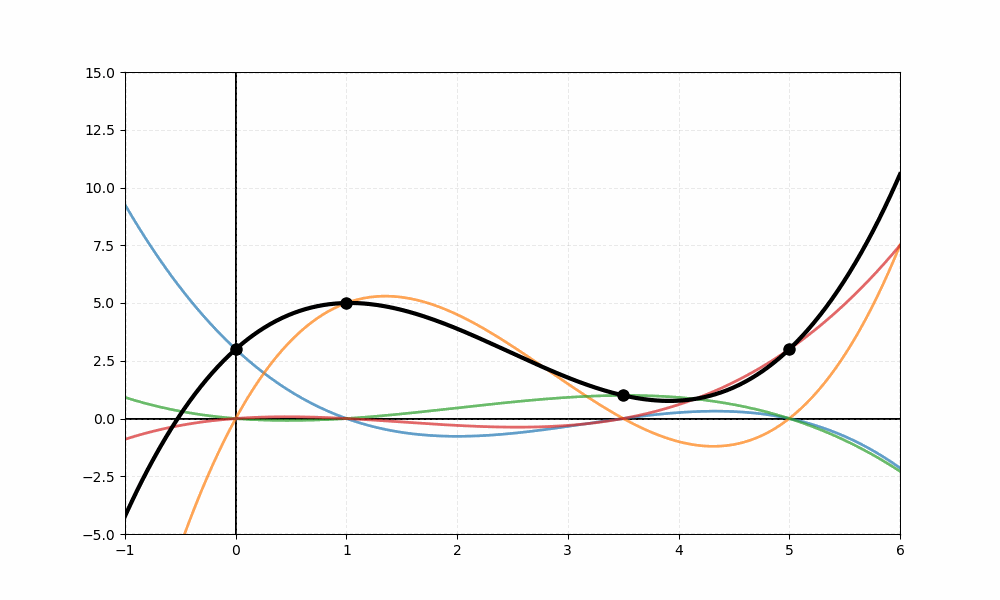 Figure 1: Lagrange interpolation reconstructing a polynomial from threshold
shares. The animation demonstrates how points uniquely determine a
polynomial of degree , enabling secret recovery.
Figure 1: Lagrange interpolation reconstructing a polynomial from threshold
shares. The animation demonstrates how points uniquely determine a
polynomial of degree , enabling secret recovery.
The visualization depicts four data points represented as black dots. The animation sequentially reveals four colored curves—each a Lagrange basis function weighted by its corresponding value, where the basis polynomial is generally defined as:
For these specific points, the four basis functions are:
The blue curve represents , orange shows , green displays , and red illustrates . In the final frame, the thick black line represents the reconstructed polynomial —the sum of all four weighted basis functions—which passes exactly through each of the four data points.